In the quest for perfection, many companies face the dilemma of selecting quality traffic in the vast digital ocean. At Mediasurfer, we prioritize using innovative approaches and technologies to safeguard the marketing interests of our clients, providing them with superior results, even in the most challenging conditions.
We employ every technical solution available to identify bot traffic. In this article, one such technology is explored.
We employ every technical solution available to identify bot traffic. In this article, one such technology is explored.
Technical solutions for bot traffic management
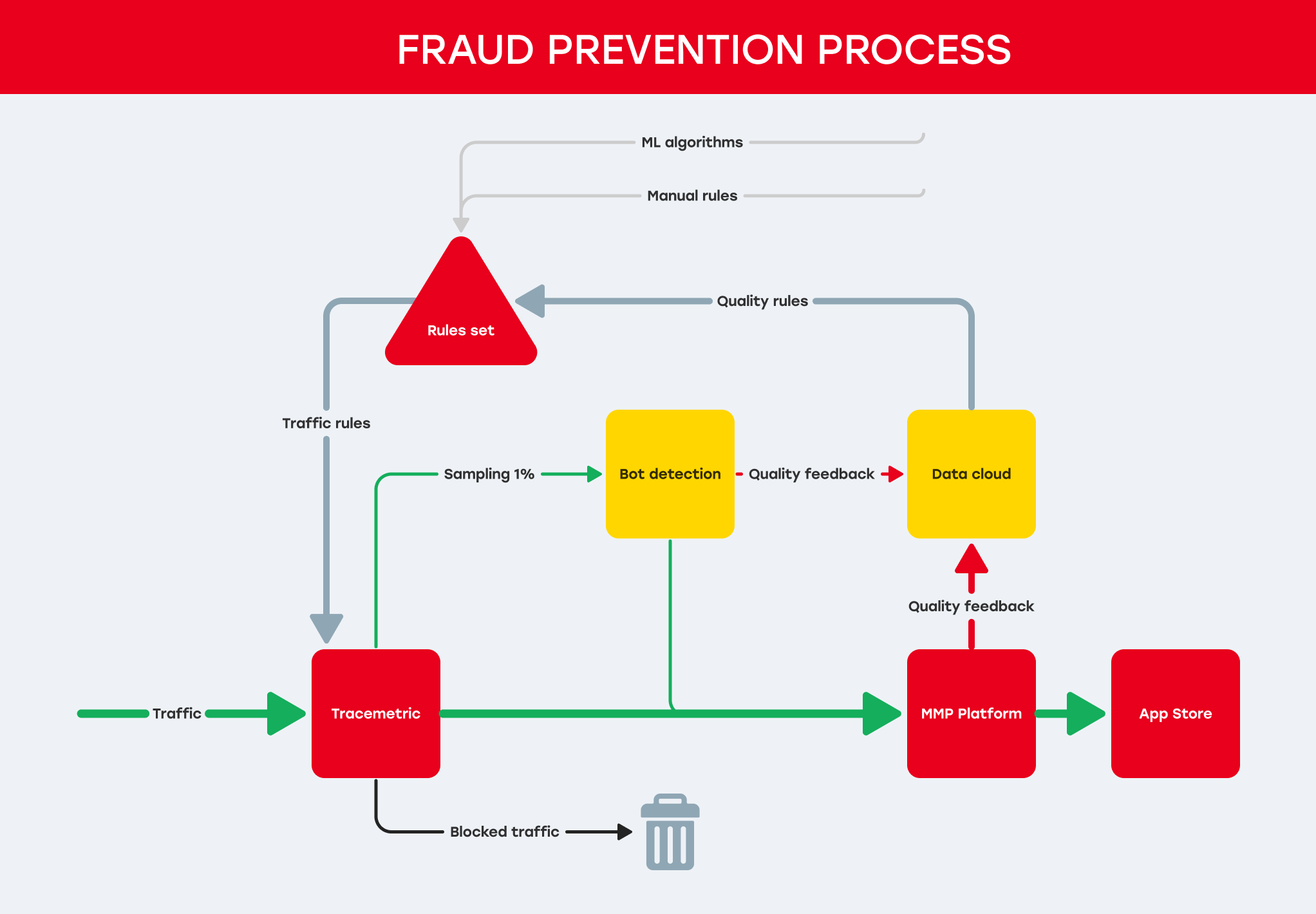
We direct part of the traffic that passes through our platform to a specially devised page. Here, the user is delayed for 1-2 seconds while the device parameters are determined. This involves a series of checks, including:
- Data from physical sensors: gyroscope, battery charge, volume
- Device parameters: video adapter, canvas-based fingerprint
- Rendering speed and individual computations
- Signs of launching in an emulator
- The correspondence of these values to normal parameters (for instance, when an emulator on Android pretends to be iOS)
This technology is similar to bank anti-fraud mechanisms and invisible CAPTCHA, which you can find on ordinary websites (e.g., Cloudflare, reCAPTCHA, etc.).
A distinct feature of in-app inventory, compared to the Web, is that not all device parameters are accessible and cookies are also absent. Current browser trends for protection against this kind of profiling do not significantly hinder operation; there are still sufficient means available to determine device parameters.
Data flow is accumulated in our cloud and used to identify suspicious traffic groups as well as signs of artificial visits.
A distinct feature of in-app inventory, compared to the Web, is that not all device parameters are accessible and cookies are also absent. Current browser trends for protection against this kind of profiling do not significantly hinder operation; there are still sufficient means available to determine device parameters.
Data flow is accumulated in our cloud and used to identify suspicious traffic groups as well as signs of artificial visits.
Balancing user experience and robust fraud prevention
A drawback of the technology is that the user must spend at least a second on a special page, which can impair user experience and conversion. Therefore, sampling occurs at random intervals and comprises 1%-5% of the total traffic volume.
This is sufficient for obtaining a picture of the quality without disrupting the regular traffic flow. In specific inventory slices, we have observed up to 40% of artificial traffic, which was blocked after verification. Providers of such traffic are promptly disconnected from advertising campaigns.
This is sufficient for obtaining a picture of the quality without disrupting the regular traffic flow. In specific inventory slices, we have observed up to 40% of artificial traffic, which was blocked after verification. Providers of such traffic are promptly disconnected from advertising campaigns.
In the upcoming sections of the article, we will delve into a more detailed discussion about other anti-fraud technologies that have been implemented by Mediasurfer.
@MEDIASURFER










